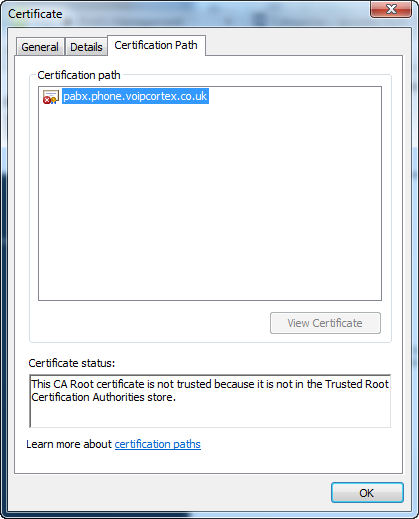
Hi Alan,
Lots of functions, especially keevio phone in 6.0 onwards require an HTTPS connection and it is a really good idea to use this exclusively for appliance administration.
The process depends on the version you are running.
From 6.0 (keevio) onwards, you can do all this from the web UI in system -> certificates:
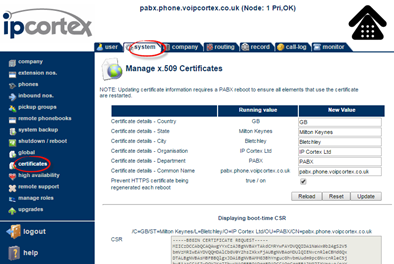
Just
- Check the box to “Prevent HTTPS certificate being regenerated each reboot”
- Enter the correct info for the certificate subject and hit the update button
- When the CSR box text changes to the new subject info, copy this text and paste into your request to the CA.
- When you get the PEM format certificate from the CA, paste this into the certificate field and hit update again (if the CA asks you to use a “certificate chain”, or “intermediate certificate”, just paste all of the certificates that they have supplied one at a time - server certificate first - into the certificate box).
- Perform a software restart on the appliance and test an https:// access, checking the returned certificate chain.
Here’s a quick video grab of the steps needed:
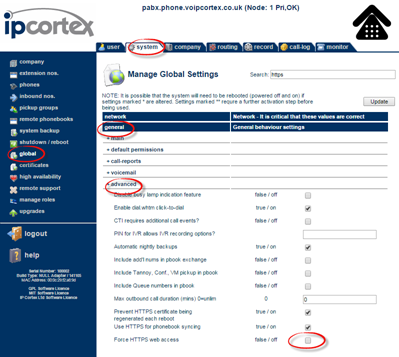
After you have done this, you may want to force all connections to HTTPS via the system -> global -> general -> advanced:
Older Releases
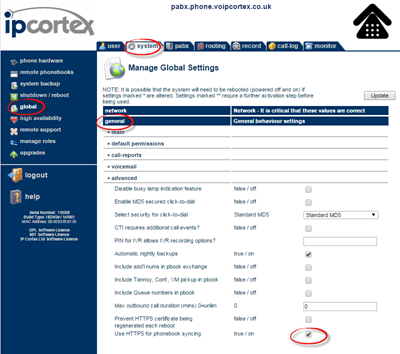
If you need to apply a certificate to a 5.1 or previous release, then you will need to do this “under the hood”
- Go to system->global->general->advanced and check “Prevent HTTPS certificate being regenerated each reboot”, and Update. Possibly do a reboot and check you get same cert fingerprint just to be safe and certain that you aren’t going to get a newly created key overwritten.
- Use openssl on the box, or on an external device to generate a new private key and CSR in PEM format in the normal way.
- Get the CSR signed by a real CA.
- Install .key in /etc/ssl/private/apache-pabx.key and .crt in /etc/ssl/certs/apache-pabx.crt - use chmod to adjust mode on /etc/ssl/private/apache-pabx.key to remove non owner read/write access if you have copied with default world readable access mode.
- Reboot the appliance and make sure all is OK by navigating to the https:// URL and checking cert chain.
Let us know if you need any further help.